There are many apps, social networks and programs that claim to offer privacy and censorship resistance, yet very few actually reach that goal (either by incompetence or malice).
Here are the red flags to look for:
Terms of services
As soon as you have to agree to any ToS before running the app or logging in, that asks you for restrictions of what you can say or do when using the app, it means that there’s a centralized control used to enforce them.
Report button
If there’s a report button somewhere to report content, then there’s centralized control in order to process them and act upon. The only valid button for unwanted messages is a block button.
No end to end encryption
If the app has no end to end encryption, its content is snooped and checked by the servers for “lawful” speech and content. It can also be processed for training AIs or sent to 3rd party contractors for analysis and “service improvements”. Beware though that even end to end encrypted services can send the data still on the device when someone presses the report button described previously. Also most metadata is not end to end encrypted (profile picture, status message, contacts, …) so make sure there’s nothing sensitive in it.

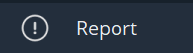
Closed source
If an app’s source code is not available, there’s no way to truly verify its implementation. The excuse usually given is that someone could recompile the app and remove the safety locks inside it, but that’s the whole point. Security must be enforced through the protocol, never on the client.
There you have it. The next time you search for a privacy conscious app, verify the above points. I made sure there’s none of those issues in the app I’m working on: Xeres.